How to avoid and deal with the ever-growing threat of ransomware
Future developments of ransomware
Ransomware currently comes in three main types – fake malware scans, screen lockers and encryption that locks you out of your computer. Only the cyber criminals controlling the encrypting ransomware have the encryption keys. They all demand payment to put things right.
Security experts are expecting and warning of self-propagating ransomware with the same kind of characteristics found in network worms, such as Conficker. In other words, ransomware is inevitable that can produce endless duplicates of itself in order to be able to spread across networks.
Furthermore, it is an easy matter for any potential cyber criminals to create or purchase their own ransomware.
Windows XP did not spread the massive Wannacry ransomware attack that hit computer networks worldwide
“No, Windows XP didn’t fuel WannaCry Scratch that idea, says Kaspersky, after mining attack detection data from PCs running its security software.” – The reason being is that the Wannacry exploit does not run on Windows XP. Actually, the main spreader of the attack across computer networks worldwide was Windows 7.
http://www.computerworld.com/article/3197703/windows-pcs/no-windows-xp-didnt-fuel-wannacry.html
Smartphone ransomware
To exploit the fact that most mobile phone users have their data backed up to the cloud, according to virtual private network (VPN) service provider NordVPN, mobile ransomware will aim at stealing users’ bank login information in order to steal funds directly from their accounts,
Apparently, some devices that use the Google Android operating system are coming preinstalled with malware that includes ransomware. The following article fills in the details.
Android devices coming with preinstalled malware –
Scareware – Fake ransomware alerts that are easy to escape
The most common type of ransomware is a con called scareware that attempts to trick users into believing that their computers have been infected with malware that can only be removed if you pay its source to remove it. A fake alert message appears (example below) or the screen displays a fake page showing a fake scan running that appears to find plenty of non-existent malware infections. The cyber criminals always demand that you pay them for a fake malware-removal tool to get rid of it.
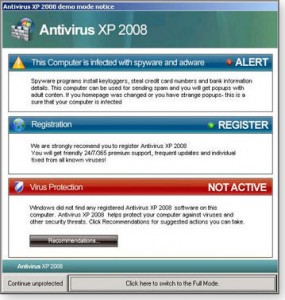
This type of malware is easy to escape from just by closing down the webpage or, if it is stuck, by closing your web browser. If necessary, bring up the Windows Task Manager ( press Ctrl + Alt + Del keys) and close the browser (Applications => Find application => End Task) – or just switch the computer off.
As a precaution always run your antivirus scanner and a system-cleaning tool
Windows keeps flagging you from its Notification Area if you don’t have a functioning antivirus scanner at work monitoring the system and updating itself automatically. Consequently, most people use one.
I always run my antivirus scanner – Avast Free Antivirus – and CCleaner, the system-cleaning tool, after something like that happens to me. Note that Avast and Malwarebytes (secondary scanner for manual scans only) usually don’t find anything wrong.
Using CCleaner to get rid of unnecessary files and Registry entries
CCleaner cleans files and has a Registry option that scans the Windows Registry for redundant entries, which can be the cause of problems.
If there are still any after-effects, if it is active (malware is able to turn it off), you could use System Restore to restore the previous day’s restore point. System Restore can be run in normal operating mode or from Safe Mode if Windows fails to boot into normal mode. A restore point with a particularly date restores the system files to those that were in use on that day.
Note that I set CCleaner not to monitor my computer and not to use “Intelligent Cookie Management” for the reasons set out in this article – CCleaner uses system monitoring and “Intelligent Cookie Management.
Note that you can only disable “Intelligent Cookie Management” during the installation of the tool. You must choose the Customize option that provides the option to disable it. The default setup installs all of the options. In other words, there is no disable option for “Intelligent Cookie Management” within the tool’s settings. CCleaner is no doubt in the pay of Google, which wants to keep its tracking cookies in place. The image below shows the install options.
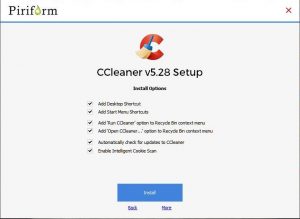
Free software almost always exacts some kind of price that usually involves installing other software, an invasion of your privacy or, in this case, the retention of the worst kind of cookies that permit online tracking.
Screen lockers
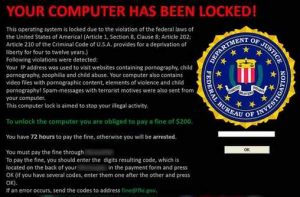
If you become the victim of a screen locker, whenever you start your computer, the screen is filled by a warning from the police, FBI or Department of Justice, etc., of the kind shown above, telling you that illegal activity has been detected on your computer and that you must pay a fine.
Note that neither the FBI nor any other kind of official policing authority would ever freeze you out of your computer or demand payment for illegal activity. They all have to go through the proper legal channels.
How to get rid of a screen locker
This kind of ransomware locks your screen and it stays locked until you restore a restore point created by System Restore, which might fix the problem, or a backup/system image, which should always fix the problem. Running an up-to-date malware scanner – which has to be run from a bootable DVD or USB flash drive because the screen is locked – may or may not fix the problem. Avast, AVG, Avira, Kaspersky, Norton, Bitdefender and Sophos all provide an antivirus boot-disk tool.
In short, if you value the data stored on your computer(s), it is now vital that you create regular backups/system images, best saved to an external hard disk drive that is disconnected from the computer(s).
Cloud storage is also an option for backup and file storage, but your data is at risk if the service you use does not use servers that are themselves using high-level encryption and multiple authentication.
If you don’t value what is stored or run on your computer(s), you can fix the problem by formatting the hard drive or SSD drive and clean-install Windows. You could also use an alternative operating system, such as the excellent Linux Mint, which, having a much smaller user base, is far less prone to any kind of malware than Windows.
Ransomware that uses encryption to lock the computer
The last type of ransomware is the most serious because it uses unbreakable encryption to lock your computer and then demands a ransom to unlock (decrypt) it. Only the cyber criminals have the encryption keys. Of course, paying the ransom is not a good idea because the cyber criminals can take your money without unlocking your computer.
I have tried very hard to get this kind of ransomware to infect a computer of mine that does not contain valuable data, but without success. However, that doesn’t necessarily mean that it is particularly difficult for an infection to take place. Reports on the web suggest that many users have become victims ransomware and lost money by paying the ransom. Moreover, always bear in mind that the threat level of this type of malware in constantly increasing in volume and sophistication.
In any case, the cyber criminals controlling the ransomware could also download files, decrypt and read them. They would then threaten to publish any private information or images if their victims fail to pay the ransom.
How to avoid a ransomware encryption infection and get rid of one
Some people will always open attachments to emails from unknown users and infect their computers. It is because of human error or dishonesty that nothing can ever be totally secure.
Many people still don’t create regular backups/ system images.
Restoring a backup is the most effective way of recovering from ransomware encryption. But you have to be able to restore a recent backup or you lose data if you don’t at least make daily copies of your files.
Most people use a malware/antivirus/spyware scanner that monitors their computer(s) in real time. Unfortunately, malware scanners won’t protect against ransomware unless they are specifically designed to do so.
The Avast malware scanner provides free ransomware protection
The Avast malware scanner provides free ransomware protection and special individual removal tools for the variants of that malware that uses encryption. This is what it says on the Avast website: “There is no better way to recognize, remove and prevent ransomware than to use an antivirus & anti-ransomware software, and the best antivirus & anti-ransomware tool is Avast.” – “Want to help prevent future ransomware infections? Download Avast Free Antivirus.