How to make sure that PC/laptop computers have no malware infections
This article deals with how to make sure that your computers have no malware infections. That they are not infected with malware and computer viruses – rogue software that users are usually tricked into installing.
For detailed information on the various types of malware infections and tricks used to get users to install them, visit the PC Security section of this website.
The best malware infections are very cunning indeed
The best malware infections are very cunning indeed. Most of the time the people – cyber criminals or the developers of unwanted software – who create them are ahead of the security companies that need to defeat them.
The security companies call software that is not harmful in any way but that most people don’t want Potentially Unwanted Programs (PUPs). Their aim is to overcome a computer system’s defences in order to be able to take control of the system. Therefore, they are programmed to conceal successful malware infections. Users install malware by clicking on an email attachment or by visiting infected websites.
Malware disguises itself as genuine software or as part of the operating system
The malware is hidden anywhere on a computer’s hard disk drive. It can disguise itself as genuine software or as part of the operating system (usually a version of Windows). Therefore, to make sure that a computer is free of rogue software in the form of viruses, Trojans, spyware, such as keyloggers, and other types of infections, every file should be scanned – engage or schedule a whole system scan – using a reputable malware scanner, at least once a week.
Ransomware malware
The worst forms of malware infections are called ransomware that comes in three main types.
The mildest and most common type of ransomware
The mildest and most common type of ransomware tries to convince the user, by presenting alarming looking graphics and warnings, that the computer in use has been scanned while online and is infected with plenty of viruses. The user is told to access a site and pay for a fix. It is a con. The user usually just has to close down the site. But it is advisable to run a full virus scan just in case the computer has been infected with malware. Every time that this has happened to me, there was no infection.
If any popups or any other after-effects occur…
If any popups or any other after-effects occur, using System Restore to restore a restore point created the day before the ransomware event occurred usually fixes the problem. It is best to use System Restore in Safe Mode to restore a restore point. Running a malware scanner, such as Malwarebytes, in Safe Mode can also fix the problem. If the user boots the system up to the boot menu (that provides all of the boot options) by pressing the F8 key startup in Windows XP/Visa/7, the Safe Mode with networking option provides online access. The user can go online search for and use a free online malware scanner. Once again, make sure that a reputable security site provides it.
Running a malware scanner in Safe Mode
Each version of Windows has its own ways of entering Safe Mode at startup or from within Windows itself. If running a malware scanner in Safe Mode or using Safe Mode with Networking to run an online scanner fails to get rid of the infection, restoring a recent system backup or image will eliminate any infection.
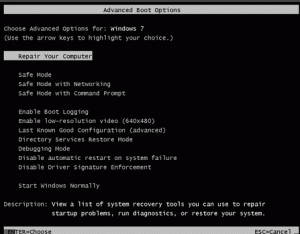
Pressing the F8 key repeatedly at startup in Windows 7 brings up the Advanced Boot Options shown in the image above. Note Windows 10 is set to boot too quickly to use the F8 key to bring up the boot menu options. The user has to enable a standard boot beforehand. The following article proves information on how to do that.
How to Boot Into Windows 10 Safe Mode –
http://www.makeuseof.com/tag/boot-windows-10-safe-mode/
Microsoft prefers Windows 10 users to make use of the latest recovery methods than to use System Restore, which is still available in Win10. For detailed information on those methods, including System Restore, read the post called How to choose the best ways to recover Windows 10 on this website.
How to boot into Safe Mode at startup and from within Windows 8.0/8.1 –
The next worse type of ransomware locks the computer’s screen and usually doesn’t allow the computer to be used in any way. A screen is usually displayed showing a law-enforcement logo with the warning that you have broken the law and must pay a fine in order to regain access to your files.
The worst type of ransomware, such as the famous CryptoLocker, encrypts and locks the computer user’s files and says that the only way to recover them is to pay a ransom. There is no need to pay a ransom because the methods mentioned earlier, that fix the mildest type of ransomware also works for the worst type.
Steps to provide the best line of defence against malware infections
Here is what to do to provide the best line of defence against malware infections:
Install one reputable malware scanner that is enabled to monitor the system in real time
1. – Install one reputable malware scanner that is enabled to monitor the system in real time, which means that it monitors the files that are in use within the system, the files that are accessed via a web browser, in an email program, being downloaded, etc. Note that Windows 8.1 and 10 uses the Windows Defender scanner by default. Windows disables it if you install another malware scanner.
Real-time scanners usually don’t check files that are unchanged. They only monitor and scrutinize the files that are actively being used or downloaded, which keeps a scanner’s impact on system performance to a minimum.
Use another malware scanner only to run manual scans
I currently use Panda Free Antivirus as my real-time monitor and the free version of Malwarebytes as a second scanner that cannot be used as a real-time system monitor. You have to buy the Pro version of Malwarebytes if you want real-time protection. Those two scanners provide protection in Windows XP up to Windows 10 [date: October 2016].
Note that a particular scanner will not detect all malware. Therefore, it is advisable to use two or more scanners. Also note that if you install two real-time scanners, make sure that you disable the real-time monitoring on one of them, because you should only have one malware scanner engaged in active monitoring. Most scanners have a setting that turns real-time monitoring off.
Windows 8.1 and 10 use Microsoft’s Windows Defender by default
Windows 8.1 and 10 use Microsoft’s Windows Defender by default. If you install another antivirus scanner, Win10 turns Windows Defender off as a real-time scanner so that two scanners won’t be working in real time doing the same activities.
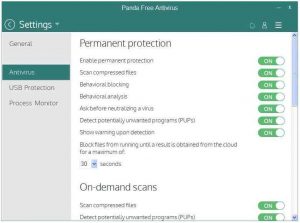
You get to the setting of most scanners by right-clicking on their icons in the Notification Area (System Tray). The image below shows the settings page of Panda Free Antivirus. Turn off the top setting called “Enable permanent protection” if you want to use Panda as a second scanner that is run manually at any time.
Schedule a daily quick scan
2. Schedule a daily quick scan set at a time when the computer is in use or not in use but switched on. The scanner might provide a setting that sets a limit, as a percentage, of the use of the processor. Microsoft Security Essentials, now only available for Windows 7, provides such a setting. If set to 50% only half of the processor’s processing power can be used during a scan. You can have a look a look at your main scanner’s settings by right-clicking on its icon in the Notification Area.
A quick scan takes a few minutes, but a full scan takes much longer because every file on every drive or partition is scanned. If you have more than one hard drive installed, it will check all of them. There should be settings that allow the user to set which drives or partitions on drives are scanned.
Most malware scanners provide an option for a custom scan
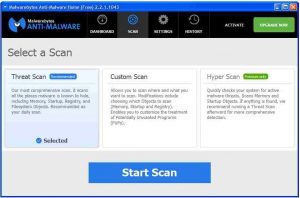
3. – Most malware scanners provide an option for a custom scan. It is advisable to schedule a full scan for once a week. The time this takes depends on how many files there are in the system and the number of tests that the scanner performs. If you keep your computers running, you can schedule times that take place when you are not using them. The image below shows the scanning options of the free Malwarebytes malware scanner, listing what it scans.
Remember that malware can be hidden anywhere on the system, not just in the areas used by the operating system. The Windows Task Scheduler, run from the Control Panel, can conveniently be used to set up a full, weekly scan when the computer is switched on but not in use. There are plenty of articles online on how to use the scheduler in Windows XP, Vista and Win7.
Schedule a scan in Windows Defender [Windows 10] –
https://support.microsoft.com/en-us/instantanswers/…
It is advisable to use a free online scanner once a month
4. – It is advisable to use a free online scanner once a month. The various makes of malware scanner have their own detection setups. One setup might detect what another setup misses, so this is a good additional measure.
Search the web for Kaspersky File Scanner (my preferred choice), Trend Micro’s House Call, Microsoft’s Safety Scanner, ESET’s Online Scanner.
Make sure that you are using a valid online malware scanner
An online scanner usually downloads and installs itself on the system; it doesn’t run from the website itself, so make sure that you are using a valid site, not a fake site made to look like one. You certainly don’t want to download and run anything from a fake website. If in doubt, the Microsoft Internet Explorer (IE) and Mozilla Firefox browsers provide an option to validate a website. In IE8, find it as follows: Tools => SmartScreen Filter => Check This Website.
It is well worth doing a full scan. I had been reading quite a bit about an exploitation by virus creators’ of a vulnerability in Java that can be used to access an infected system from a remote location, so I used MSE to perform a full scan. I wasn’t expecting it to find anything because MSE never found anything during a daily quick scan and it was monitoring the system in real time. However, to my great surprise, it found three viruses that exploit Java vulnerabilities that it gave a Severe designation, which means that they are dangerous to system security and should be removed immediately.
Somehow my computer had been infected by the vulnerability of the Java Virtual Machine
In short, somehow my computer had been infected by the vulnerability of the Java Virtual Machine (JVM) that runs the Java code that is used by some websites, so I changed all of the accounts that I log into with only a user name and password. I use an Ubuntu boot disc to access banking sites that cannot be influenced by malware, so I didn’t need to change their login information. The only banking site that I use that needs only an email address and password is PayPal. All of the other banking sites I use require a unique access number that can only be used once, obtained via a machine in my possession that I insert an access card into that then itself requires a PIN. Other banking sites require the user to obtain the access number sent to a registered mobile phone.
Uninstall Java, because few websites use it and it can pose a very serious security risk
Having heard of the Java vulnerabilities, I had uninstalled every Java installation (use Add or Remove Programs in Windows XP and Programs & Features in Vista and Windows 7), but I hadn’t deleted the Java folder, using Windows Explorer, which was located at:
C:\Documents and Settings\Application Data\Sun\Java
MSE found the three viruses in the Java folder, so I made it remove them and then deleted the Sun folder. Here are the names of those viruses that you might like to search for on the web:
JAVA/CVE-2012-1723.ED
JAVA/CVE-2012-1723.EE
JAVA/Blacole.GI
It is advisable to uninstall Java, because few websites use it and it can pose a very serious security risk. I uninstalled it years ago and have never had to use it. If a website that you use regularly tells you that it requires Java to function, you can download and install it from java.com.
Java places its control panel in the Windows Control Panel if it is installed from a download from java.com. When installed, you have to enable Java in every browser you use.
How do I enable Java in my web browser? –