What data encryption is and what you need to know about it
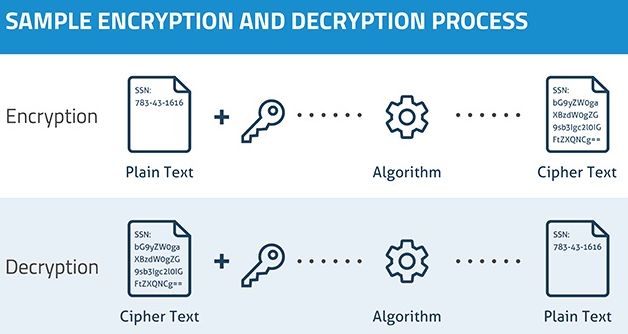
Data encryption is a system designed to encode (scramble) a transfer of data or a web connection so that if it is intercepted it cannot be read or viewed by anyone who doesn’t have the decryption key that unscrambles it back into its original state so that it can be read or viewed.
The use of encryption is essential to keep the web a secure place in which to conduct business or transfer data. Ordering goods, banking, etc., involves providing login information, email addresses, credit-card members, etc. That private information is kept away from prying eyes by using encryption, preventing identity theft and other cyber crimes.
Hardware and software data encryption
Data encryption is provided by hardware implementation, such as the built-in encryption that an SSD drive provides, or by software implantation using the Bitlocker application that some versions of Windows Vista/7/8.1/10 provide. (Free and paid-for software encryption applications are also available.)The following article provides more information about hardware and software data encryption.
A serious SSD encryption issue in Windows 10 when using Bitlocker encryption software –
Secure https:// URLs
Any website that has https:// (instead of the insecure plain http://) at the front of its URL address is using encryption between that website and its users.
HTTPS Is Almost Everywhere. So Why Isn’t the Internet Secure Now? –
https://www.howtogeek.com/397043/https-is-almost-everywhere.-so-why-isnt-the-internet-secure-now/
You can add additional security by using software such as IBM Security Trusteer Rapport that can be set to protect any website from many kinds of attacks, such as keylogging and taking screenshots from remote locations. Note that it does not currently support the Google Chrome web browser, but might at a later date. Its website’s support page, provided at the end of this article, provides a link to a page that lists supported browsers.
IBM Trusteer Rapport Technical Support –
http://www.trusteer.com/support
The two main data encryption systems
There are two main systems used to encrypt data. The Symmetric Key system uses the same public key at both ends to encrypt and decrypt. There are many doors that can be chosen from and the site sending the encrypted data tells the computer receiving the information at the start which door is being used. Anyone spying on the connection, who also has the private key, would have to find out which specific door is being used. There are so many doors that this cannot be achieved in time. The other system is for the sender site to use a private key that only it has and the receiver to use a public key. A mixture of the two systems can be used. The following video provides an illustrated basic explanation of both systems.
Symmetric Key and Public Key Encryption –
Read the following article for more detailed information on how data encryption works:
How Encryption Works –
http://computer.howstuffworks.com/encryption.htm
Data encryption back doors
The countries apparently being targeted by terrorists have made know their hatred of encryption. They say that it allows terrorists to hide their communications from the West’s security services, therefore, they are pressing the web companies that allow encryption to be used, such as Google and Apple, to build back doors into their encryption so that the security services can monitor encrypted communications as if they were unencrypted.
Fortunately, there are people in high places, such as the CEO of Apple, Tim Cook, who can see the danger of having backdoor access to encrypted communication, which would be much like having a master key or password.
You can’t have a back door that’s only for the good guys
Tim Cook said in a recent interview: “You can’t have a back door that’s only for the good guys.”
Search the web for that quote to read what he said. It was widely reported. It is a warning that if the good guys can build back doors into encrypted communications, the bad guys could figure out how to hack into them and gain as much information as the security services. That is, they could steal user names and passwords, bank account and credit card numbers and their three-digit security numbers, social-security numbers, telephone numbers, social media, DNA records, medical records, login information, etc., etc.
I don’t use encryption to encrypt files, folders or hard-disk or SSD drives, I just don’t put any information in them that could be used by cyber criminals to access my accounts or steal my identity. Nor for that matter do I give Facebook, or Twitter (Google Plus – G+ – is due to shut down) that kind of information. Why should any of them know your address, phone number, etc. unless it is a business page that customers need to contact?
Use a notebook for your usernames and passwords hidden somewhere in your home
It’s much better to have a notebook hidden somewhere inside your house or office containing the user names and passwords for websites than to have them listed in files on a computer. That way, I know that if any of my computers is stolen no one would be able to use any information on it to their advantage and/or my disadvantage. To me, that is preferable to having encrypted files, folders or whole drives that could become inaccessible should I lose the encryption keys. I also don’t use methods such as fingerprint login to computers because Facebook, Google, the security services and cyber criminals could get hold of that information. I am law-abiding, so I see no reason for anyone have my DNA or fingerprints.
Add to all of this the fact that there are attempts being made by the West’s liberal metropolitan elite to control the web that could be used to prevent free speech. The following video is worth watching in that regard.
Free Internet Speech In Danger – Dick Morris TV: Lunch Alert! –
http://www.dickmorris.com/free-internet-speech-in-danger-dick-morris-tv-lunch-alert/